Während sich die USA auf das Feiertagswochenende um den vierten Juli vorbereiteten, nutzte die Ransomware-Gruppe REvil eine Schwachstelle in der Kaseya Software, um Managed Service Provider (MSPs) und deren Kunden anzugreifen. Mindestens 1.500 Unternehmen scheinen betroffen zu sein, auch solche, die keine direkte Beziehung zu Kaseya haben.
Zum Zeitpunkt der Erstellung dieses Artikels scheint es, dass eine Zero-Day-Schwachstelle genutzt wurde, um Zugang zu den Kaseya VSA-Servern zu erhalten, bevor Ransomware auf den von diesen VSA-Servern verwalteten Endpunkten installiert wurde. Dieser Modus Operandi unterscheidet sich deutlich von früheren Ransomware-Kampagnen, bei denen es sich in der Regel um von Menschen durchgeführte, direkte Kompromittierungen handelte.
Die nachstehende Analyse bietet Darktrace Einblicke in die Kampagne anhand eines Beispiels aus der Praxis. Sie zeigt, wie die selbstlernende KI den Ransomware-Angriff erkannte und wie Antigena die Kundendaten im Netzwerk vor der Verschlüsselung schützte.
Analyse der REvil-Ransomware aus der Netzwerkperspektive
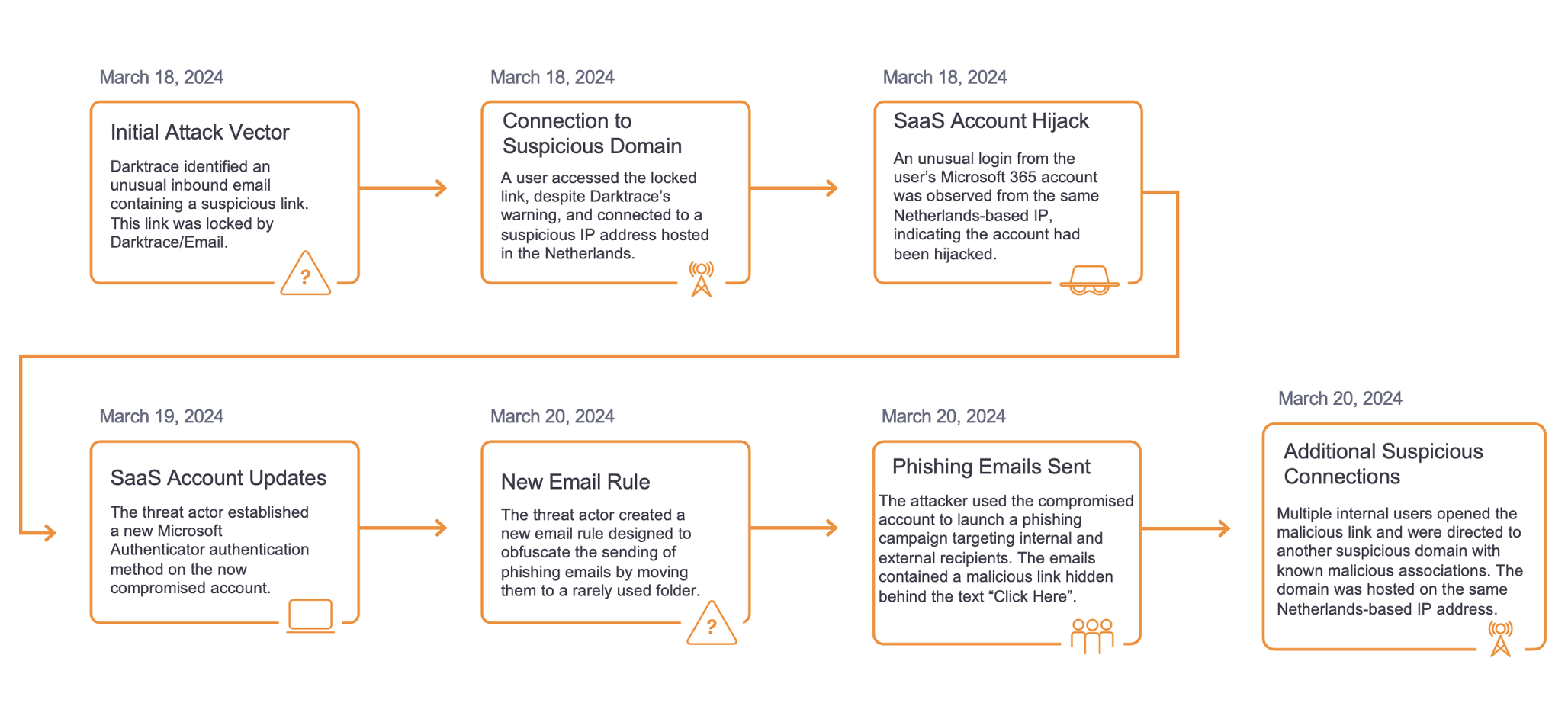
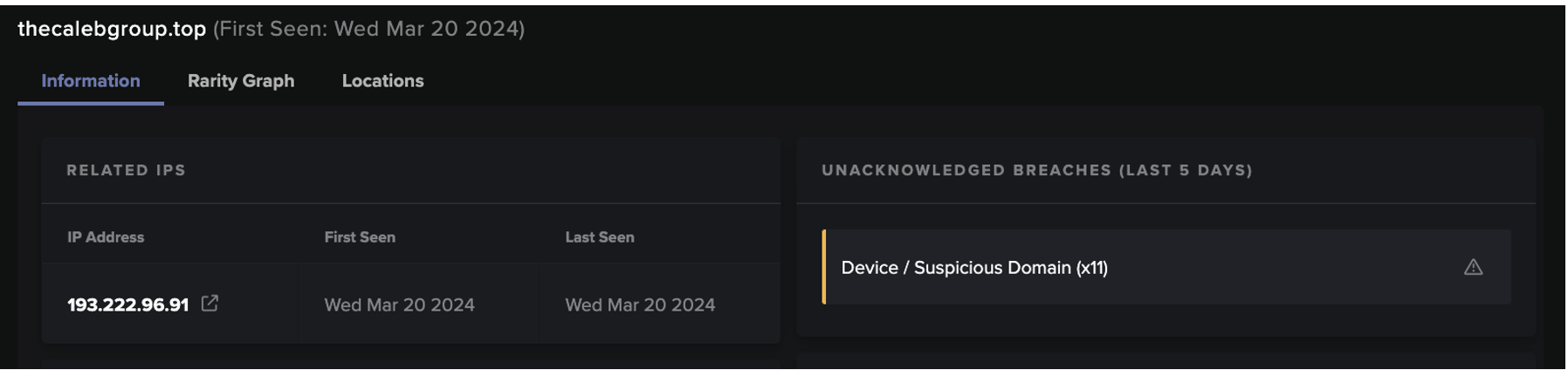
Antigena erkannte die ersten Anzeichen von Ransomware im Netzwerk, sobald die Verschlüsselung begonnen hatte. Die folgende Grafik zeigt den Beginn der Ransomware-Verschlüsselung über SMB-Freigaben. Als die Grafik aufgenommen wurde, fand der Angriff live statt und war noch nie zuvor gesehen worden. Da es sich um eine neuartige Bedrohung handelte, stoppte Darktrace die Netzwerkverschlüsselung ohne statische Signaturen oder Regeln.

Die Ransomware begann um 11:08:32 Uhr zu agieren, was durch die Meldung "SMB Delete Success" (SMB-Löschung erfolgreich) vom infizierten Laptop an einen SMB-Server angezeigt wurde. Während der Laptop manchmal Dateien auf diesem SMB-Server liest, löscht er nie diese Art von Dateien auf dieser speziellen Dateifreigabe, so dass Darktrace diese Aktivität als neu und ungewöhnlich erkannte.
Gleichzeitig erstellte der infizierte Laptop den Erpresserbrief "943860t-readme.txt". Auch hier handelte es sich bei dem "SMB Write Success" auf dem SMB-Server um eine neue Aktivität - und Darktrace suchte nicht nach einer statischen Zeichenfolge oder einem bekannten Erpresserbrief. Stattdessen erkannte es - durch vorheriges Lernen des "normalen" Verhaltens jeder Einheit, Peer Group und des gesamten Unternehmens - dass die Aktivität ungewöhnlich und neu für diese Organisation und dieses Gerät war.
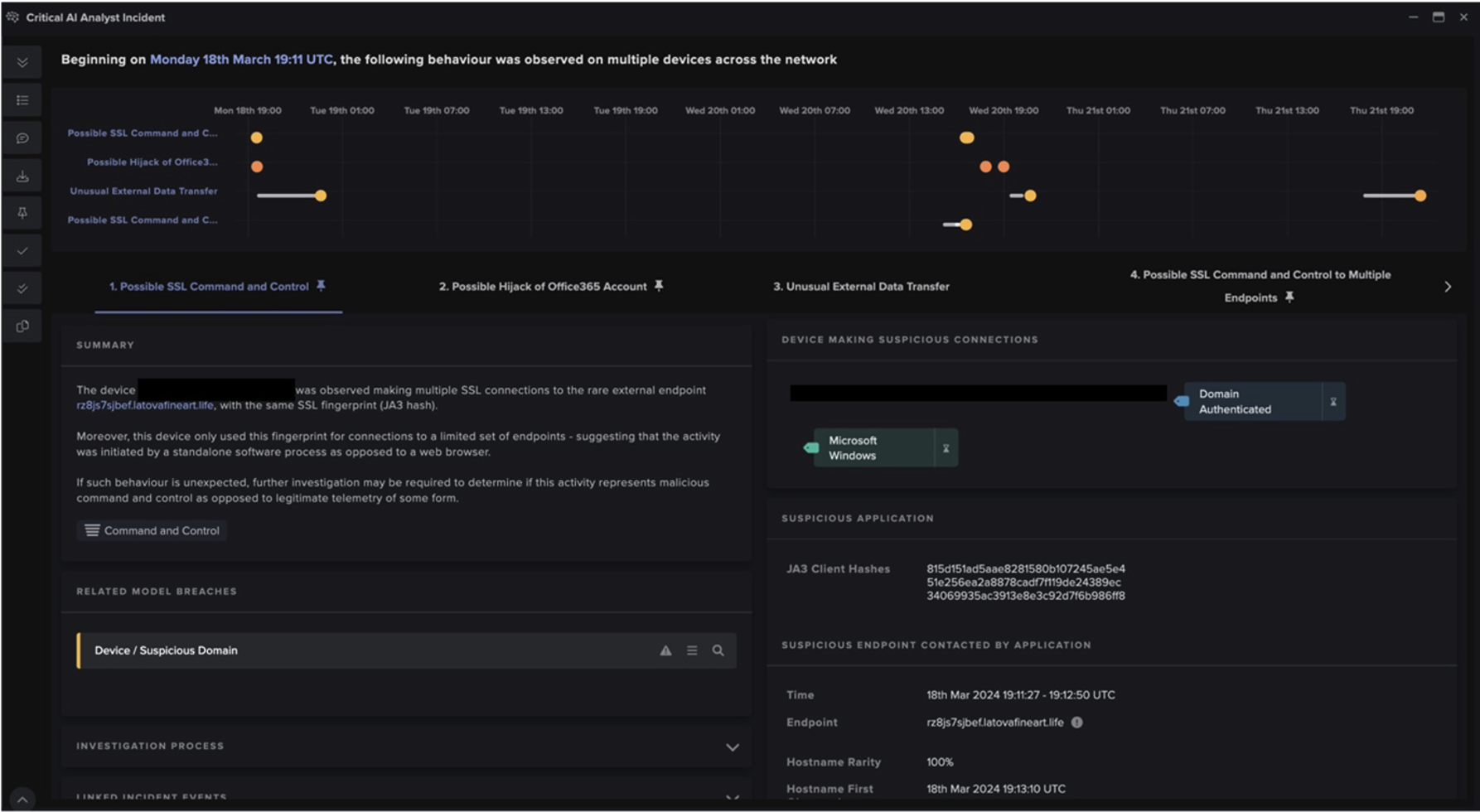
Durch die Erkennung und Korrelation dieser subtilen Anomalien identifizierte Darktrace die frühesten Stadien der Ransomware-Verschlüsselung im Netzwerk und Antigena ergriff sofortige Maßnahmen.

Antigena machte zwei präzise Schritte:
- Erzwingen der gelernten "pattern of life" (Verhaltensmuster) für fünf Minuten: Dadurch wurde verhindert, dass der infizierte Laptop neue oder ungewöhnliche Verbindungen herstellt. In diesem Fall wurde jede weitere neue SMB-Verschlüsselungsaktivität verhindert.
- Gerät für 24 Stunden unter Quarantäne stellen: Normalerweise würde Antigena nicht so drastische Maßnahmen ergreifen, aber es war klar, dass diese Aktivität dem Verhalten von Ransomware sehr ähnlich war. Daher beschloss Antigena, das Gerät im Netzwerk vollständig unter Quarantäne zu stellen, um zu verhindern, dass es weiteren Schaden anrichtet.
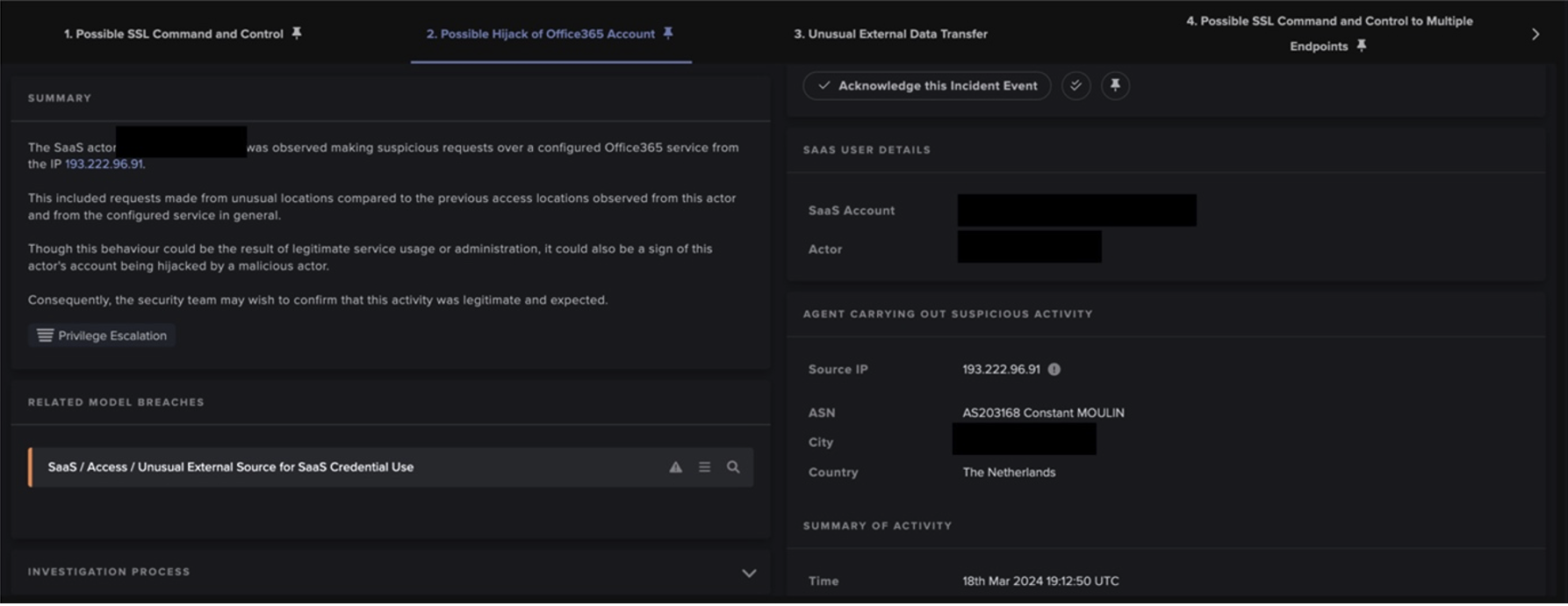
Mehrere Minuten lang versuchte der infizierte Laptop immer wieder, sich über SMB mit anderen internen Geräten zu verbinden, um die Verschlüsselung fortzusetzen. Dieser Versuch wurde von Antigena in jeder Phase blockiert, wodurch die Ausbreitung des Angriffs begrenzt und der durch die Netzwerkverschlüsselung verursachte Schaden gemindert werden konnte.

Auf technischer Ebene lieferte Antigena die Blockierungsmechanismen über die Integration mit nativen Sicherheitskontrollen, wie z. B. bestehenden Firewalls, oder indem es selbst aktiv wurde, um die Verbindungen zu unterbrechen.
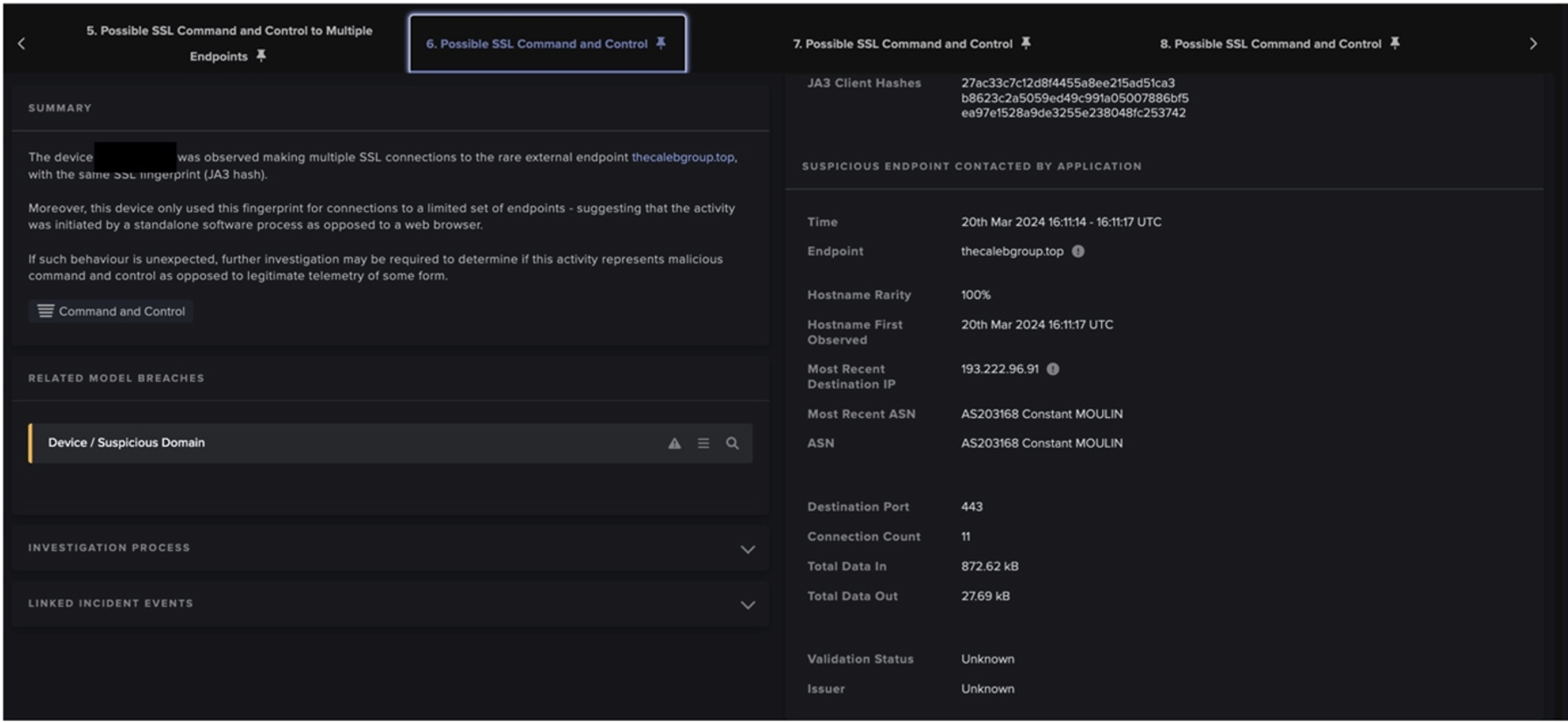
Die folgende Grafik zeigt das "Lebensmuster" für alle Netzwerkverbindungen des infizierten Laptops. Die drei roten Punkte stehen für die Erkennungen von Darktraceund zeigen den genauen Zeitpunkt an, zu dem die Ransomware REvil auf dem Laptop installiert wurde. Die Grafik zeigt auch einen abrupten Stopp der gesamten Netzwerkkommunikation, als Antigena das Gerät unter Quarantäne stellte.

Angriffe werden immer vorkommen
Während des Vorfalls fand ein Teil der Verschlüsselung lokal auf dem Endgerät statt, auf das Darktrace keinen Zugriff hatte. Außerdem war der Kaseya VSA-Server, der ursprünglich kompromittiert wurde, via Internet in diesem Fall für Darktrace nicht sichtbar.
Dennoch erkannte die selbstlernende KI die Infektion, sobald sie das Netzwerk erreichte. Dies zeigt, wie wichtig es ist, sich gegen aktive Ransomware im Unternehmen zu schützen. Unternehmen können sich nicht nur auf eine einzige Verteidigungsschicht verlassen, um Bedrohungen abzuwehren. Ein Angreifer wird immer - irgendwann - in Ihre Umgebung eindringen. Die Verteidigung muss daher ihren Ansatz zur Erkennung und Schadensbegrenzung ändern, sobald ein Angreifer in das Netzwerk eingedrungen ist.
Vielen Cyberangriffen gelingt es, die Endpunktkontrollen zu umgehen und sich aggressiv in Unternehmensumgebungen zu verbreiten. Autonomous Response kann in solchen Fällen selbst bei neuartigen Kampagnen und neuen Malware-Stämmen für Ausfallsicherheit sorgen.
Dank der selbstlernenden KI konnte die Ransomware des REvil-Angriffs keine Verschlüsselung über das Netzwerk durchführen, und die im Netzwerk verfügbaren Dateien wurden gesichert. Dazu gehörten auch die kritischen Dateiserver des Unternehmens, auf denen Kaseya nicht installiert war und die daher die ursprüngliche Nutzlast nicht direkt über das bösartige Update erhielten. Durch die Unterbrechung des Angriffs in dem Moment, in dem er stattfand, verhinderte Antigena, dass Tausende von Dateien auf Netzwerkfreigaben verschlüsselt wurden.
Weitere Beobachtungen
Exfiltration von Daten
Im Gegensatz zu anderen REvil-Angriffen, die Darktrace in der Vergangenheit aufgedeckt hat, wurde keine Datenexfiltration beobachtet. Dies ist interessant, da es sich von dem allgemeinen Trend des letzten Jahres unterscheidet, bei dem sich cyberkriminelle Gruppen im Allgemeinen mehr auf die Exfiltration von Daten konzentrieren, um ihre Opfer zu erpressen, da diese immer bessere Back-up Strukturen aufbauen.
Bitcoin
REvil hat eine Gesamtzahlung von 70 Millionen Dollar in Bitcoin gefordert. Für eine Gruppe, die versucht, ihre Gewinne zu maximieren, erscheint dies aus zwei Gründen seltsam:
- Wie soll ein einzelnes Unternehmen 70 Millionen Dollar von potenziell Tausenden von betroffenen Organisationen eintreiben? Sie müssen sich der enormen logistischen Herausforderungen bewusst sein, die damit verbunden sind, auch wenn sie von Kaseya erwarten, dass es als zentrale Anlaufstelle für das Einsammeln des Geldes fungiert.
- Seit DarkSide den Zugang zu den meisten Colonial Pipeline Lösegeldern verloren hat, sind Ransomware-Gruppen dazu übergegangen, Zahlungen in Monero statt in Bitcoin zu verlangen. Monero scheint für die Strafverfolgungsbehörden schwieriger zu verfolgen zu sein. Die Tatsache, dass REvil Bitcoin, eine besser verfolgbare Kryptowährung, verwendet, scheint kontraproduktiv für ihr übliches Ziel der Gewinnmaximierung zu sein.
Ransomware-as-a-Service (RaaS)
Darktrace bemerkte auch, dass andere, traditionellere "Großwildjagd"-Ransomware-Operationen von REvil am selben Wochenende stattfanden. Dies ist nicht überraschend, da REvil ein RaaS-Modell betreibt. Daher ist es wahrscheinlich, dass einige Partnergruppen ihre regulären Angriffe fortsetzten, während der Angriff auf die Kaseya-Lieferkette im Gange war.
Unberechenbar ist nicht Unverteidigbar
Am Wochenende des vierten Juli gab es große Angriffe auf die Lieferkette von Kaseya und separat auf den kalifornischen Distributor Synnex. Die Bedrohungen kommen aus allen Richtungen und nutzen Zero-Days, Social-Engineering-Taktiken und andere fortschrittliche Tools.
Die obige Fallstudie zeigt, wie selbstlernende Technologie solche Angriffe erkennt und den Schaden minimiert. Sie fungiert als wichtiger Teil der Tiefenverteidigung, wenn andere Schichten - wie Endpunktschutz, Bedrohungsdaten oder bekannte Signaturen und Regeln - unbekannte Bedrohungen nicht erkennen können.
Der Angriff erfolgte in Millisekunden, schneller als jedes menschliche Sicherheitsteam reagieren konnte. Autonomous Response hat sich als unschätzbar wertvoll erwiesen, wenn es darum geht, diese neue Generation von Bedrohungen in Maschinengeschwindigkeit abzuwehren. Es schützt Tausende von Unternehmen auf der ganzen Welt 24/7 und stoppt jede Sekunde einen Angriff.
Abweichungen von Darktrace Modellen
- Compromise / Ransomware / Suspicious SMB Activity
- Compromise / Ransomware / Suspicious SMB File Extension
- Compromise / Ransomware / Ransom or Offensive Words Written to SMB
- Compromise / Ransomware / Ransom or Offensive Words Read from SMB