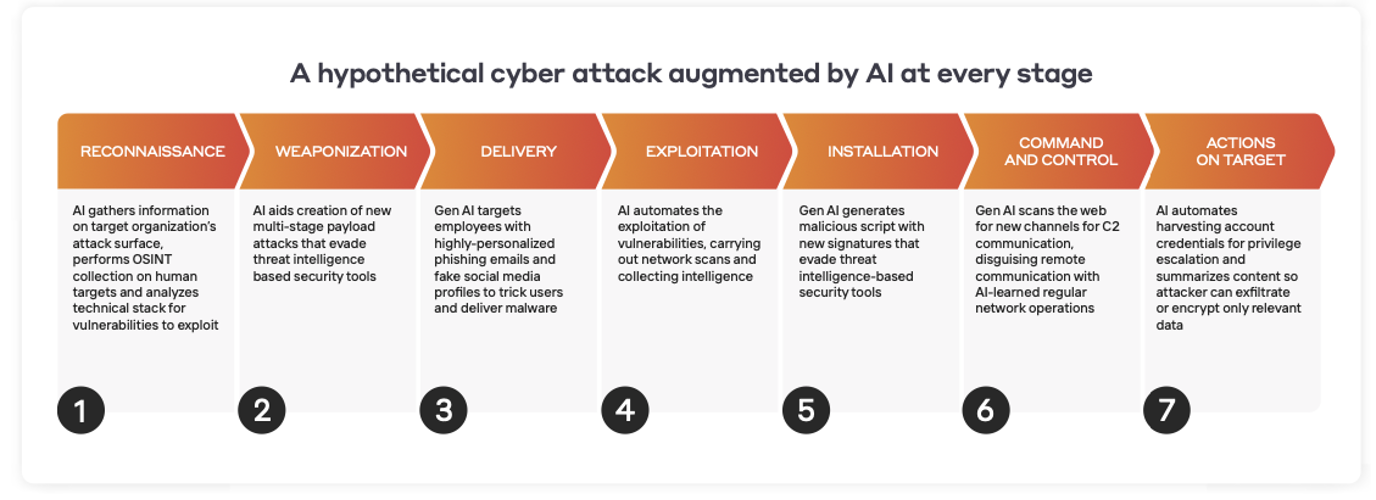
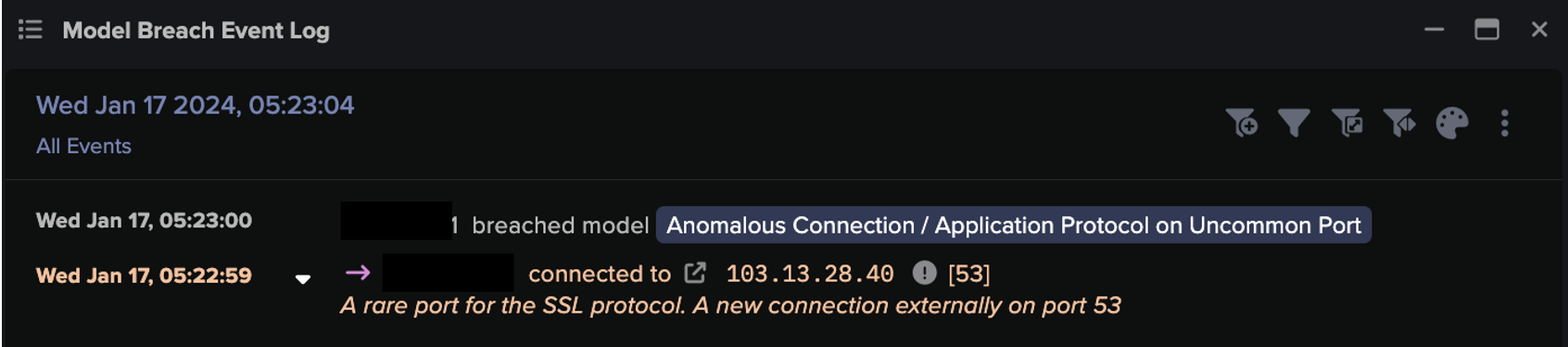
In parallel to the global COVID-19 pandemic, there has been a growing ransomware pandemic. Darktrace researchers discovered that ransomware attacks on US organizations tripled in 2021 compared to 2020, and attacks on UK organizations doubled.
This crisis brought 30 nations together to discuss a counter-ransomware initiative focused on cryptocurrency regulation, security resilience, attack disruption, and international cyber diplomacy. Despite these landmark policies and law enforcement efforts, it’s safe to say that ransomware will remain as a top priority threat and is not going anywhere.
As ransomware permeates, cyber-attackers will continue evolving techniques in 2022
Ransomware gangs are becoming more sophisticated in how they select targets and how they carry out attacks. Many organizations think that ransomware shouldn’t be a serious concern if they have backups in place because they can quickly bring business operations back online. But modern attacks are about more than encryption or data exfiltration; they focus on maximizing disruption to business operations, including targeting backups for encryption and deletion. In 2022, we could see ransomware gangs target cloud service providers as well as backup and archiving providers.
Critical infrastructure organizations and businesses will continue to assess how quickly they can restore operations in the aftermath of an attack and how extensively they will be able to rely on, and the costs required for cyber insurers to cover entire ransom payments and costly systems repairs.
In early January, Microsoft researchers found evidence of malware targeting multiple Ukrainian organizations deploying what appeared to be ransomware but was actually a wiper. The malware displays a ransom note then executes the wiper when the target device is powered down. If adopted by other non-state actors, this evolution goes beyond ransomware, and some organizations won’t be able to survive these types of attacks.
Sophisticated ransomware gangs will expand their detailed targeting efforts from only ‘big game hunting,’ where they target large and well-known targets, to use more resources directly targeting midsize and smaller organizations. With increased scalability through automation and leveraging supply chain attacks, ransomware gangs will have the resources to expand their operations. Large organizations have more substantial budgets and more people, and they can prioritize resources to deal with ransomware’s effects — it will be far more difficult for small businesses.
Not only are ransomware operators expanding whom they can target, but the group of cyber-attackers able to execute attacks is expanding. The rise of Ransomware-as-a-Service (RaaS) gives low-skilled threat actors access to sophisticated malware strains, lowering the barrier to entry for attackers. RaaS has expanded the criminal ecosystem to include lower-level threat actors who find and attack the targets before installing the malicious software. Threat actors are increasingly using bots to automate the initial attack that gets them a foothold in the system.
There is also a varying degree of professionalism amongst cyber-criminals, from seasoned veterans (with current or previous nation-state experience) to ‘script kiddies’ with little expertise. This array translates to greater potential for untested or reckless use of sophisticated tools by unsophisticated actors.
Ransomware groups will bounce back
Ransomware groups are resilient. Even if government pressures force ransomware groups to disband or criminally charge them, they will continue to rebrand and crop back up. For example, DarkSide, confirmed by the FBI to be behind the attack on Colonial Pipeline, shut down a week after the attack. Shortly after, BlackMatter emerged, widely believed to be a rebranded version of the same cyber-crime group.
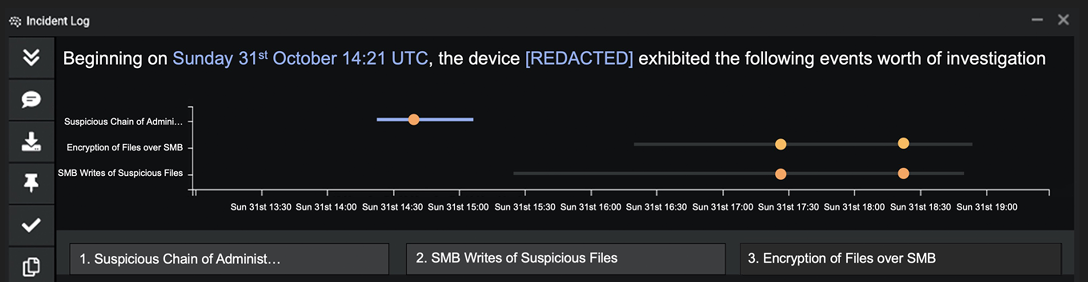
Figure 1: Darktrace breaks down the stages of a BlackMatter ransomware attack targeting a marketing firm in the US
Earlier this year, Russia’s security agency announced that it had arrested several members belonging to the notorious REvil ransomware gang and neutralized its operations. While this is a significant step against a major group, it is unlikely to reflect a long-term change in Russian policy towards cyber-criminal gangs. These arrests almost certainly do not mark the end of REvil.
Five ransomware groups have formed a cartel to exchange data and ‘best’ practices. These groups include Wizard Spider (linked to the Ryuk and Conti ransomware strains), Twisted Spider (which developed Maze and uses Egregor), Viking Spider (the group behind Ragnar), and LockBit.
Even if government pressures force ransomware groups to disband or criminally charge ransomware gangs, these groups will continue to rebrand and crop back up with even more sophisticated techniques and capabilities.
A static ‘hardened’ perimeter defense isn’t the answer – a dynamic self-defending one is
For organizations to build systems to withstand cyber-attacks, security leaders need to think and, more importantly, defend beyond the initial breach to maximize continuity of business operations. Security defenses like firewalls centered on defending the cyber perimeter are not enough to protect against evolving threats.
A truly dynamic defense is achievable. Organizations need to actively enforce ‘normal’ for businesses and disrupt attacks at the earliest indicators of malicious anomalous behavior, such as file encryption or data exfiltration. Security technology needs to learn, make micro-decisions, and take proportional responses to detect and stop attacks early enough before data exfiltration or encryption occurs.
Attackers are acutely aware of Threat Intelligence-reliant defensive tools they need to evade and know the limitations of the legacy, siloed approach many organizations employ. Attackers are finding valuable information, exfiltrating the files, and encrypting the data in a short period. The race condition and response window for defenders to detect and stop attacks is getting smaller; security teams and solution responses must get faster.
Cyber security is no longer a human-scale problem. Organizations need to adopt AI-based protections that can defend against increasingly automated ransomware attacks. In an era of fast-moving cyber-attacks, and with threat actors deliberately striking when security teams are out of the office, AI technologies have become essential in taking targeted action to contain attacks without interrupting normal business.